Best Mobile Penetration Testing Company In Mumbai
We Secure Your Apps
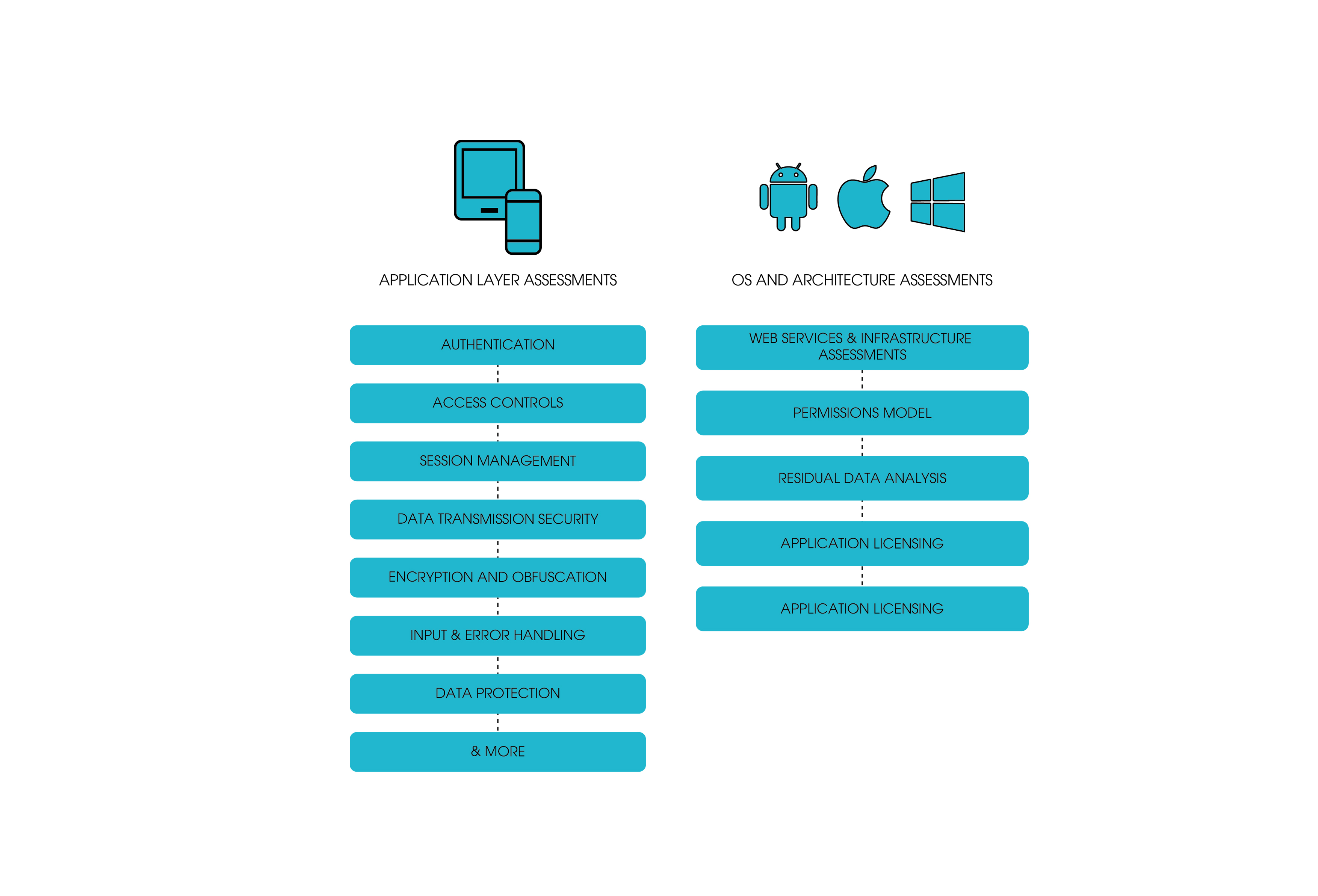
Our mobile application security testing service provides in-depth security testing of mobile applications to conform with the high security standards. We test the application for technical, logical vulnerabilities and industry best practices to provide a detailed report with proof of concepts. Detailed remediation procedures are also included to the report to fix the issues.
01.
Pre-engagement interactions
We understand your mobile app through multiple interactions in the pre-engagement process and ensure we identify your critical data and core competencies.
02.
Threat Modeling
We understand your mobile application through multiple rounds of interactions in the pre-engagement process and ensure we identify your critical data and core competencies.
03.
Static Analysis
We will perform reverse engineering on your app to extract the source code. We perform extensive source code analysis to identify sensitive information that are vulnerable to exploitation
04.
Dynamic Analysis
We follow OWASP Mobile Top 10 based vulnerability assessments. We install your app in real devices and perform real time attacks to ensure that your mobile app is secure.
05.
Exploitation
Our White hat hackers will try to exploit the vulnerabilities identified during the analysis phase and estimate the extent of losses that are possible through the identified bugs.
06.
Reporting
We provide a comprehensive mobile application security report that’s understandable by your dev team. We work with your team to fix the identified loopholes.